Optimize & Unify Security Operations
Optimize security operations by consolidating processes, organizing and prioritizing tasks and coordinating staff to achieve your security mission.

Common Use Cases
Explore the range of use cases that we can cover for you. Click on them to see the solution templates that we have ready.


Unified Security
Processes & Procedures
Manage all your security operations processes with a single platform. Document your security operations mission and goals, capture detailed procedures to ensure preparedness, and centrally manage critical security threat responses. Monitor threat intelligence, track risks to the organization and create and implement plans for coordinated responses.




Track Threats And
Coordinate Responses
Defend against unauthorized activity by tracking threat feeds, monitoring intrusion detection data, and capturing threat analysis results. Assign research and response activities with integrated task management.


How SmartSuite Works For Your Teams
Marketing powered by our Work Management Platform puts unprecedented capability at your fingertips. Start easy, then enjoy 200+ features built to help you work the way you want.

Heading
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.
Solution Tab Link Text


Understand Your Security Posture
Tailor reports and dashboards for teams and executives at every level. Track workflow, monitor cyber security risks and mitigate threats.
Solution Tab Link Text
Understand Your Security Posture
Tailor reports and dashboards for teams and executives at every level. Track workflow, monitor cyber security risks and mitigate threats.
Solution Tab Link Text
Be Agile and Effective
Assign and prioritize operational activities. Keep an eye on critical incidents and their mitigation efforts in a single view without using multiple tools and spreadsheets.
Solution Tab Link Text
Be Agile and Effective
Assign and prioritize operational activities. Keep an eye on critical incidents and their mitigation efforts in a single view without using multiple tools and spreadsheets.
Solution Tab Link Text
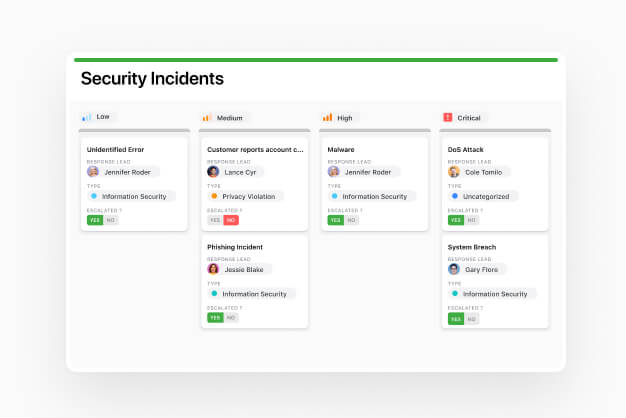
Prioritize Your Response
Rapidly respond to a range of incidents, from cyber security attacks to vulnerability identification and remediation. Use Automations to expedite security incident workflows, schedule maintenance and assessments, and more.
Solution Tab Link Text
Prioritize Your Response
Rapidly respond to a range of incidents, from cyber security attacks to vulnerability identification and remediation. Use Automations to expedite security incident workflows, schedule maintenance and assessments, and more.
Solution Tab Link Text
Have Critical Conversations In Context
Communicate with your entire security team in real-time, right where experts are conducting analysis or interpreting data.
Solution Tab Link Text
Have Critical Conversations In Context
Communicate with your entire security team in real-time, right where experts are conducting analysis or interpreting data.
Solution Tab Link Text
Receive Real-Time Incident Notifications
Ensure high-priority issues or events receive immediate attention from your operations staff.
Solution Tab Link Text
Receive Real-Time Incident Notifications
Ensure high-priority issues or events receive immediate attention from your operations staff.
Solution Tab Link Text
Integrate With Your Security Tools
Integrate with external systems to bring scan summaries or critical event data directly into SmartSuite. Create tasks for the security team when your ticketing system indicates a potential security issue.
Solution Tab Link Text
Integrate With Your Security Tools
Integrate with external systems to bring scan summaries or critical event data directly into SmartSuite. Create tasks for the security team when your ticketing system indicates a potential security issue.
Solution Tab Link TextCybersecurity Ops

Data Protection
Protect personal information by utilizing the data protection template. Monitor and control access to your most sensitive data.

Security Events
Collect, assign and manage security events.

Physical Security Policies
Establish the rules for granting, control, monitoring and removing physical access to offices or facilities. Use this solution to identify sensitive areas within the organization and define access to them.

Policy Management
Centralize your company policies to easily author, review and publish to your entire workforce from one place.
















