Streamlined Security Management
Protect your people and personal property, safeguard your equipment and make sure your team stays safe. Create a comprehensive physical security plan that coordinates technology, hardware and operating procedures to protect from threats, intrusions and breaches.

Common Use Cases
Explore the range of use cases that we can cover for you. Click on them to see the solution templates that we have ready.





Evaluate
Every Security Risk
Assess your organization for potential risks, possible weaknesses or gaps in detection. Review access control measures, security procedures for important assets and devices and put together remediation plans to address identified issues to continually improve your program.
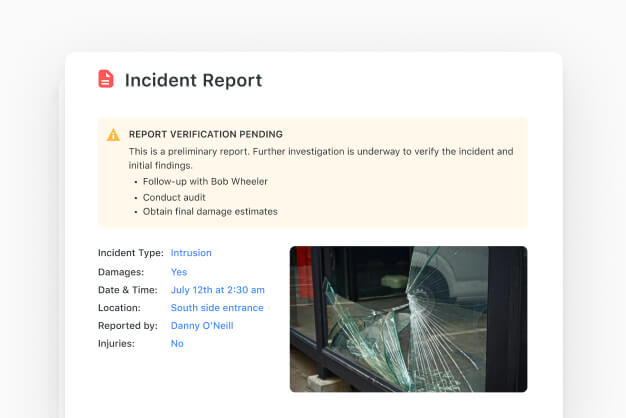
How SmartSuite Works For Your Teams
Marketing powered by our Work Management Platform puts unprecedented capability at your fingertips. Start easy, then enjoy 200+ features built to help you work the way you want.

Heading
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.
Solution Tab Link Text


Manage Security Staff & Scheduling
Make sure your spaces and assets are secure at all times with staff management functions like scheduling and task assignment. Get instant availability to operating information and procedures from any device.
Solution Tab Link Text
Manage Security Staff & Scheduling
Make sure your spaces and assets are secure at all times with staff management functions like scheduling and task assignment. Get instant availability to operating information and procedures from any device.
Solution Tab Link Text
Instantly View Your Security Posture
Make reports and dashboards available to teams at every level of the organization, demonstrating the status of security operations, initiatives and incidents. Monitor key risks and issues and understand your organization’s level of preparedness and the results of security testing.
Solution Tab Link Text
Instantly View Your Security Posture
Make reports and dashboards available to teams at every level of the organization, demonstrating the status of security operations, initiatives and incidents. Monitor key risks and issues and understand your organization’s level of preparedness and the results of security testing.
Solution Tab Link Text
Seamlessly Integrate Your Security Systems
Leverage SmartSuite’s powerful import and integration capabilities to interoperate with security systems. Integrate with security surveillance systems, user-management platforms and more to give your security team immediate access to the data they need to do their job effectively.
Solution Tab Link Text
Seamlessly Integrate Your Security Systems
Leverage SmartSuite’s powerful import and integration capabilities to interoperate with security systems. Integrate with security surveillance systems, user-management platforms and more to give your security team immediate access to the data they need to do their job effectively.
Solution Tab Link Text
Get Real-Time Notifications Of Critical Events
Let security personnel know about critical security incidents to streamline response. Alert key team members when elements of your security program require assessment to ensure that emerging threats are properly met and any deficiencies are addressed.
Solution Tab Link Text
Get Real-Time Notifications Of Critical Events
Let security personnel know about critical security incidents to streamline response. Alert key team members when elements of your security program require assessment to ensure that emerging threats are properly met and any deficiencies are addressed.
Solution Tab Link Text
Rely On Our Secure, Always-On System
Trust that your security operations data is safe and secure on infrastructure that employs industry best practices and comprehensive privacy policies. Our cloud-based system ensures that your information is always available and accessible in an instant.
Solution Tab Link Text
Rely On Our Secure, Always-On System
Trust that your security operations data is safe and secure on infrastructure that employs industry best practices and comprehensive privacy policies. Our cloud-based system ensures that your information is always available and accessible in an instant.
Solution Tab Link Text
Audit Every Piece Of Data
Log every system interaction, from administrative changes through any data entry or change by security personnel. All data is available for audit, and can be easily exported to make it available to analyze in an external tool or to provide to law enforcement.
Solution Tab Link Text
Audit Every Piece Of Data
Log every system interaction, from administrative changes through any data entry or change by security personnel. All data is available for audit, and can be easily exported to make it available to analyze in an external tool or to provide to law enforcement.
Solution Tab Link TextPhysical Security
Visitor Tracker
Step beyond the antiquated front-desk and paper-based sign-in. Visitors log their information and teammates receive automated messages notifying them a visitor has arrived.

Physical Security Policies
Establish the rules for granting, control, monitoring and removing physical access to offices or facilities. Use this solution to identify sensitive areas within the organization and define access to them.

Project Risks & Issues
Centralize project risk and issues to ensure mitigation and resolution actions are effectively deployed. Capture cross-functional data to analyze and eliminate root cause issues tripping up your projects.

IT Security Policies
Create, maintain and share rules and procedures for all individuals accessing and using an organization’s IT assets and resources.















